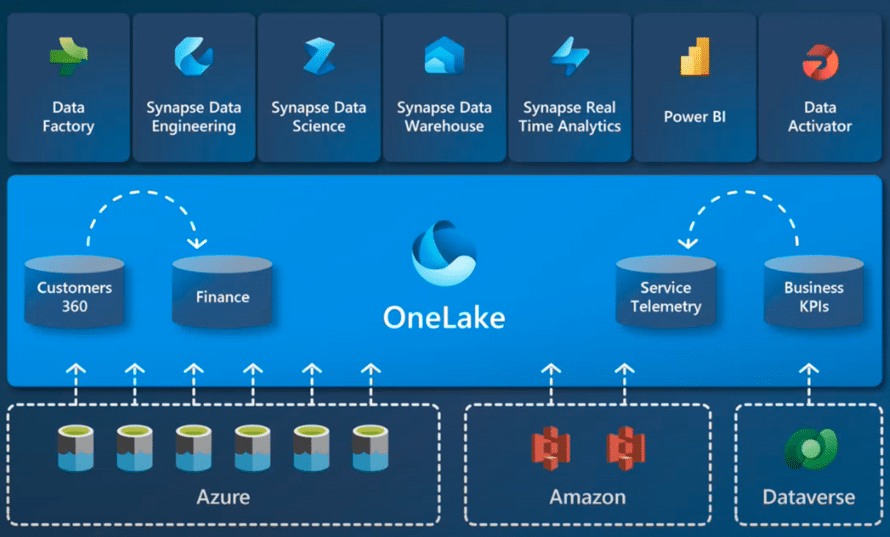
Microsoft Fabric for Dynamics 365: What You Need to Know
Microsoft Fabric is changing the way organizations operate with their data, centralizing ingestion, transformation, visualization, and insights so organizations can […]

Microsoft Fabric is changing the way organizations operate with their data, centralizing ingestion, transformation, visualization, and insights so organizations can […]
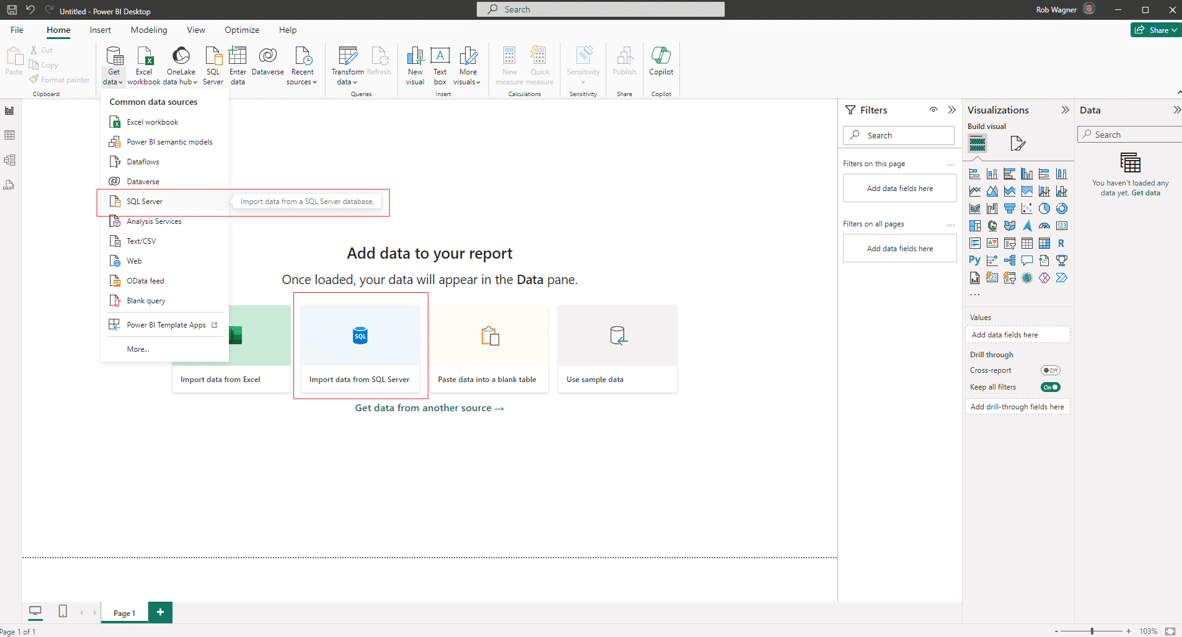
Creating actionable intelligence from your Dynamics GP data can be accomplished with the robust features and functionalities in Power BI. […]

Finding a partner who can help you navigate Dynamics 365 licensing will help you make sense of the various options […]
Efficient and effective distribution operations in today’s technology-driven environment hinge on fully harnessing the available capabilities of your software and […]
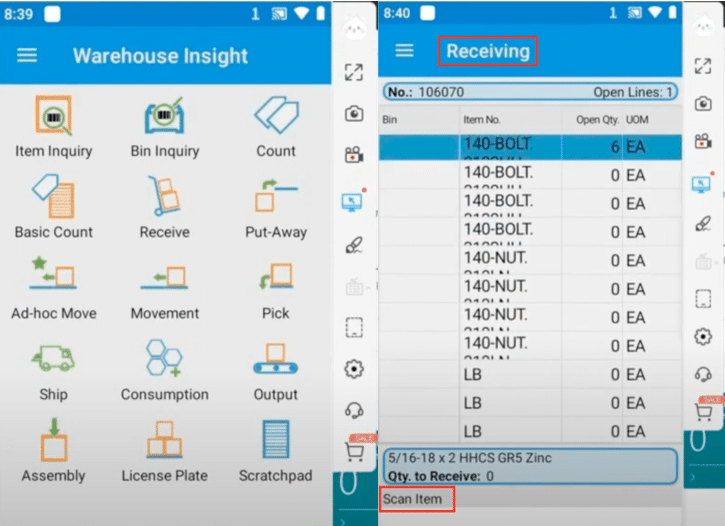
Navigating the distribution operations landscape requires precision and effective tools. Dynamics 365 Business Central offers a comprehensive suite of features […]
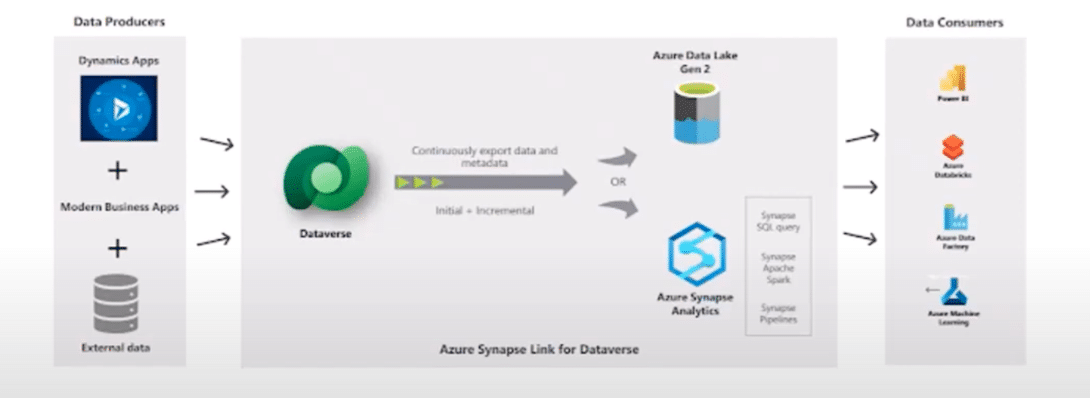
With news that Microsoft is deprecating Export to Data Lake, a popular upgrade to replace this system has emerged in […]
Enterprise resource planning (ERP) is a system that integrates various business processes and functions into a single platform. ERP implementation […]

For nonprofits and nongovernmental organizations (NGOs) navigating grants and awards, selecting the right software is paramount to efficient fund management. […]
Microsoft has launched a new range of commercial Microsoft 365 and Office 365 plans that exclude Teams, called “(no Teams)”. […]
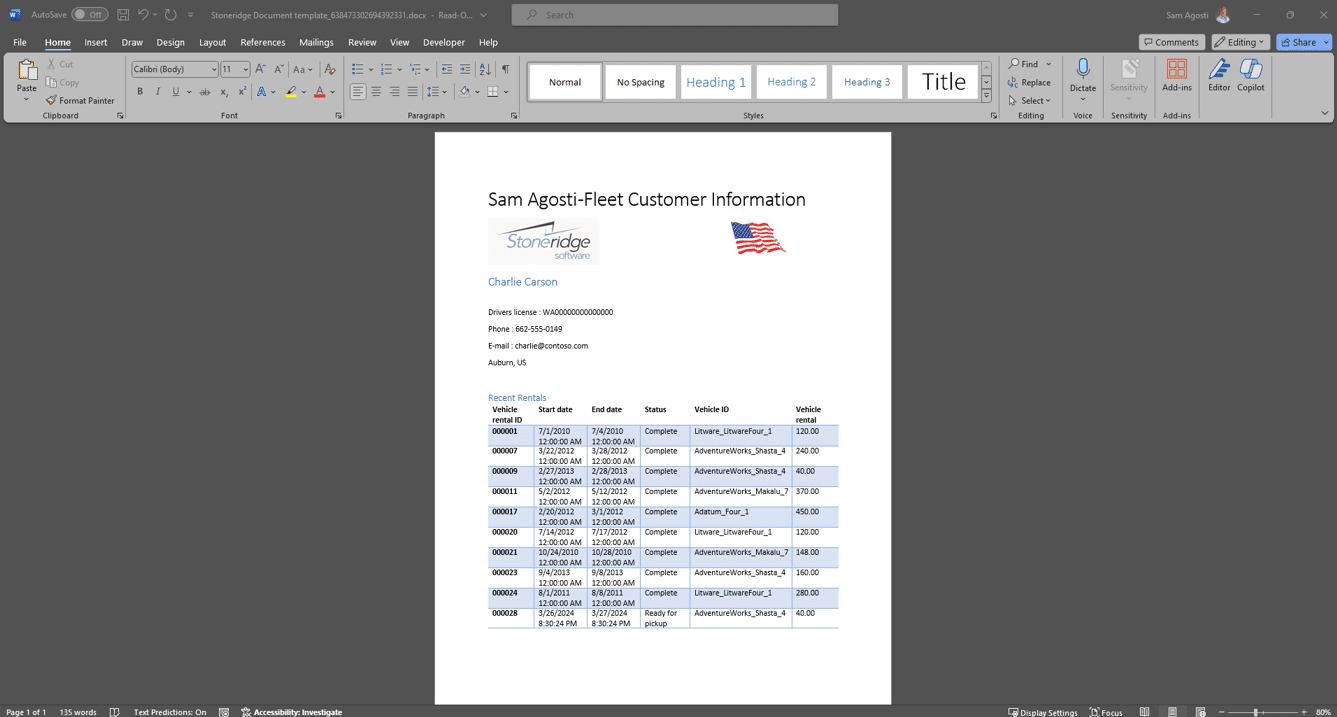
Creating and using document templates in Dynamics 365 Finance and Operations is an efficient way to generate standardized documents populated […]
It’s our mission to help clients win. We’d love to talk to you about the right business solutions to help you achieve your goals.